The Russian hacktivist alliance “Matryoshka 424” has announced the inclusion of Team ARXU, a prominent pro-Bangladeshi hacktivist group. This alliance,…
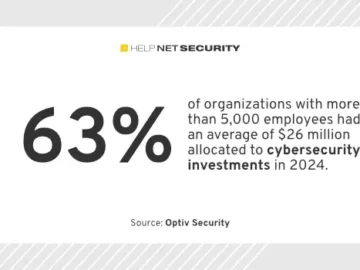
Most companies do not know how effectively they are investing money to fight the cybersecurity threat, according to Optiv. Cybersecurity…
The Australian Digital Health Agency (ADHA) is attempting to scale up its healthcare identifiers service through a new five-year roadmap….
In this Help Net Security, Martin Reynolds, Field CTO at Harness, discusses how AI can enhance the security of software…
Jul 03, 2024NewsroomMalware / Threat Intelligence An unnamed South Korean enterprise resource planning (ERP) vendor’s product update server has been…
Secator is an open-source task and workflow runner tailored for security assessments. It facilitates the use of numerous security tools…
Jul 03, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered an attack campaign that targets various Israeli entities with publicly-available…
The Rafel RAT is an advanced Android-targeting Remote Access Trojan which poses a great cybersecurity danger. This malicious program has…
CISO Atera | Israel | On-site – View job details The CISO will oversee our company’s information, cyber, and technology…
The Android Security Bulletin details security vulnerabilities affecting Android devices, where devices with security patch levels of 2024-07-05 or later…
Booktopia has entered voluntary administration after struggling with the expense of transitioning to a $12 million robot-enabled warehouse facility and to…
A Pakistan-linked hacking group has unleashed an updated version of its Android spyware, expanding its reach to target mobile gamers,…