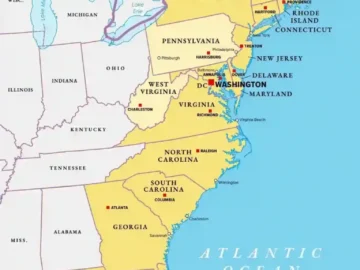
The U.S. Atlantic States Marine Fisheries Commission (ASMFC) has acknowledged a data breach and begun to notify customers who were…
Google has launched kvmCTF, a new vulnerability reward program (VRP) first announced in October 2023 to improve the security of…
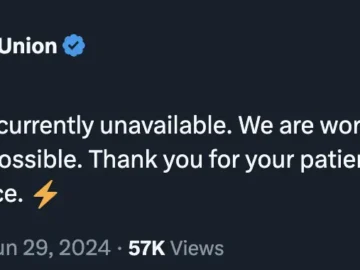
Patelco Credit Union, one of the oldest and largest credit unions in the U.S., fell victim to a ransomware attack…
Buy now, pay later loan company Affirm is warning that holders of its payment cards had their personal information exposed…
The FBI has issued a Private Industry Notification (PIN) warning of vulnerabilities in the US Renewable Energy Sector to cyber-attacks….
Cybersecurity teams probably have their work cut out right now, just looking at Ransomware Attacks alone. Every 14 Seconds, a…
CSHARP-STREAMER, a Remote Access Trojan (RAT), was identified during an investigation of a ransomware attack using Metaencryptor, with a Powershell…
Cisco has disclosed a critical vulnerability in its widely-used NX-OS network operating system that could allow attackers to execute arbitrary…
In February 2024, Prudential Financial reported it had fallen victim to a ransomware attack. The attack was discovered one day…
Multiple owners of Google Pixel 6 series phones (6, 6a, 6 Pro) have been reporting in the past week that…
Multiple vulnerabilities in the CocoaPods dependency manager have been identified, posing a significant risk of supply chain attacks. The flaw…
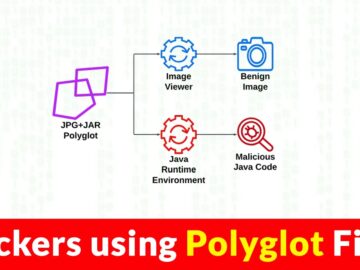
Polyglot files have to fit in several file format specifications and respond differently depending on the calling program. This poses…