Modern Intel processors, including chips from the Raptor Lake and the Alder Lake generations are susceptible to a new type…
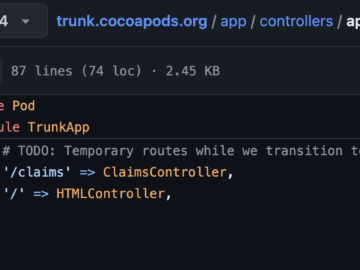
Jul 01, 2024NewsroomSupply Chain / Software Security A trio of security flaws has been uncovered in the CocoaPods dependency manager…
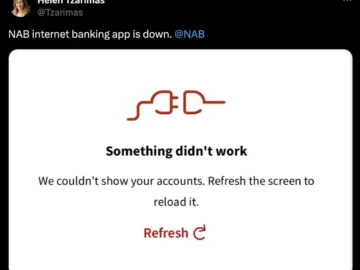
An executive from National Australia Bank says the country’s four major banks are under constant attack, with threat actors launching…
An Australian man faces charges for setting up fake Wi-Fi networks (“evil twins”) to steal data from unsuspecting travelers at…
The Australian Federal Police (AFP) have charged a man for setting up fake free WiFi access points in order to…
CocoaPods vulnerabilities reported today could allow malicious actors to take over thousands of unclaimed pods and insert malicious code into…
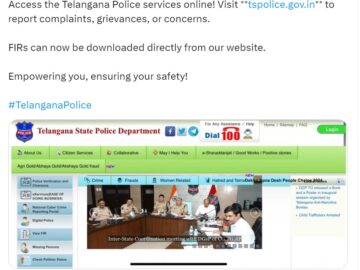
Nearly a month after The Cyber Express exposed a data breach in the digital assets of India’s Telangana State Police, the…
HubSpot, a prominent American CRM and marketing software company, has initiated an investigation following a cyber attack that potentially compromised…
Data sovereignty is about the legal ability to control how data can be shared and used. Sounds simple, but how…
This week on the Lock and Code podcast… More than 20 years ago, a law that the United States would…
Enterprises are missing out on some cost-effective, easy wins when it comes to delivering on sustainable IT goals, data from…
Critical unauthenticated remote code execution flaw in OpenSSH server Pierluigi Paganini July 01, 2024 A critical flaw in the OpenSSH…