We believe in fostering an environment where everyone feels valued and empowered to be their authentic selves, both in and…
The Black Suit ransomware gang claimed a recent cyberattack on KADOKAWA corporation and is now threatening to publish stolen data…
Amazon’s cloud division has launched an investigation into Perplexity AI. At issue is whether the AI search startup is violating…
Queensland Rail has recruited Darren Cavanagh from Transport for NSW as its group executive of digital and information. Queensland Rail…
Crypto scammers hijacked Channel 7 News Australia’s YouTube account to run a live stream of an Elon Musk deepfake on…
CSIRO has taken the wraps off a new Dell-built high-performance computer (HPC) cluster called Virga. Image credit: CSIRO Virga has…
Overview of NIST 800-53, FISMA, and FedRAMP The National Institute of Standards and Technology (NIST) is a U.S. federal agency…
The Australian Taxation Office (ATO) will next month move from biannual to daily ingestion of data from Services Australia to…
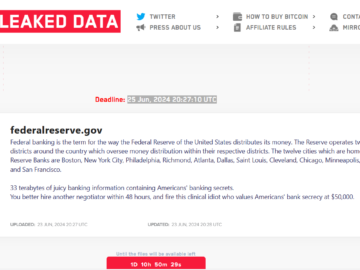
LockBit group wrongly claimed the hack of the Federal Reserve Pierluigi Paganini June 27, 2024 The LockBit ransomware group seems…
Services Australia has opened the myGov application to veteran services following a major funding boost in the federal budget. Through…
Specifically, we are looking at Reflected XSS (RXSS) in e-commerce services. According to the 7th Annual Hacker-Powered Security Report, Reflected…
Claims, counterclaims, website shutdowns, redirections and DDoS attacks were among the highlights (or lowlights) as news of the Polyfill supply…