THIS ARTICLE IS republished from The Conversation under a Creative Commons license. The US military recently launched a groundbreaking initiative…
29 Jun 3 Cybersecurity Stocks That Could Make Your Grandchildren Rich Posted at 08:29h in Blogs by Di Freeze This…
WIRED learned this week that Amazon Web Services investigated claims that the AI search startup Perplexity may have violated the…
Netflix is renowned for its diverse and engaging lineup of drama-filled shows that cater to a wide array of audiences….
A new survey, “Cyber Insurance and Cyber Defenses 2024: Lessons from IT and Cybersecurity Leaders,” highlights the impact of cyber…
Transitioning to SAP Cloud offers many advantages—from improved performance to easier data models—but it also increases a couple of inherent…
Hackers target and abuse npm packages to inject malicious code into widely used software libraries, reaching many developers and applications….
Microsoft and Proximus Group have formally signed a 5-year strategic partnership, allowing both companies to strengthen their digital lead and…
Internet of Things (IoT) devices—ranging from everyday sensors and smart gadgets to sophisticated appliances—have seamlessly integrated into our lives, enhancing…
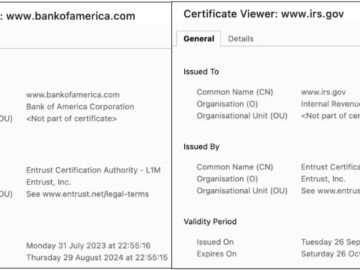
Google’s Chrome browser is making a significant security move by distrusting certificates issued by Entrust, a prominent Certificate Authority (CA),…
Marketing and sales software giant HubSpot announced on Friday that it is investigating a cybersecurity incident following reports of customer…
The Queensland government is offering up to $50 million in grants as part of a “comprehensive quantum strategy”. The funding…