China-linked spies target Asian Telcos since at least 2021 Pierluigi Paganini June 20, 2024 A China-linked cyber espionage group has…
Car dealership SaaS platform CDK Global suffered an additional breach Wednesday night as it was starting to restore systems shut…
1inch, a leading DeFi aggregator that provides advanced security solutions to users worldwide, has announced today the launch of the…
1inch, a leading DeFi aggregator that provides advanced security solutions to users across the entire space, has announced today the…
Hunting for Volt Typhoon, a sophisticated and stealthy cyber threat actor with unknown malware components “living off the land”, is…
Jun 20, 2024NewsroomFirmware Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched security flaw in Phoenix SecureCore UEFI…
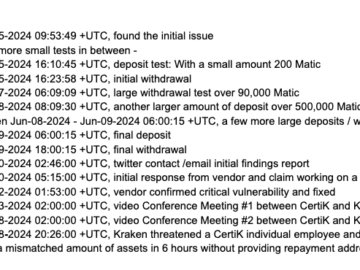
In a high-stakes clash within the crypto verse, Kraken, a leading U.S. cryptocurrency exchange, has accused blockchain security firm Certik…
Dubai, UAE, June 20th, 2024, CyberNewsWire 1inch, a leading DeFi aggregator that provides advanced security solutions to users across the entire…
Ohio-based Crown Equipment, which is among the largest industrial and forklift truck manufacturers in the world, has become a victim…
Private healthcare company Bupa, which provides health and insurance services to 7.2 million people in Australia and the Asia-Pacific (APAC)…
On March 31st, 2024, The Payments Card Industry Standards Security Council (PCI SSC) officially retired version 3.2.1 of the PCI…
MSP leaders are advised to save the date for June 27. In a special session, called “3 Security Trends to…