Chrome to distrust Entrust certificates by November 2024! Learn why some websites might show security warnings & what you, as…
TeamViewer, a remote monitoring and management tool based in Germany, has reported a security breach within its internal corporate IT…
Jun 28, 2024NewsroomSoftware Security / DevOps GitLab has released security updates to address 14 security flaws, including one critical vulnerability…
Hackers have claimed three prominent cyberattacks in Italy in the last 24 hours. The Italy ransomware attacks were allegedly carried…
RMM software developer TeamViewer says a Russian state-sponsored hacking group known as Midnight Blizzard is believed to be behind a…
In this podcast, we look at artificial intelligence (AI) and data storage with Grant Caley, UK and Ireland solutions director…
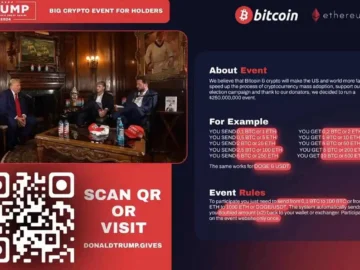
A convincing live stream featuring a seemingly-legitimate Donald Trump YouTube channel quickly gained massive traction, reaching nearly half the number…
Geisinger, a prominent healthcare system in Pennsylvania, has announced a data breach involving a former employee of Nuance, an IT…
Unless you’re an accountant, the whole end-of-year tax filing can be a nightmare. While you might look forward to your…
The recent large scale supply chain attack conducted via multiple CDNs, namely Polyfill.io, BootCDN, Bootcss, and Staticfile that affected anywhere from…
28 Jun Top 10 Cybersecurity Leaders To Follow On LinkedIn In 2024 Posted at 08:54h in Blogs by Di Freeze…
The modern kill chain is eluding enterprises because they aren’t protecting the infrastructure of modern business: SaaS. SaaS continues to…