Dell Technologies is assembling half of the racks for the supercomputer that xAI is building, billionaire Elon Musk said in…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified numerous vulnerabilities in traditional virtual private network (VPN) solutions that…
Advance Auto Parts has confirmed it suffered a data breach after a threat actor attempted to sell stolen data on…
Google Chrome 126 update addresses multiple high-severity flaws Pierluigi Paganini June 19, 2024 Google released Chrome 126 update that addresses…
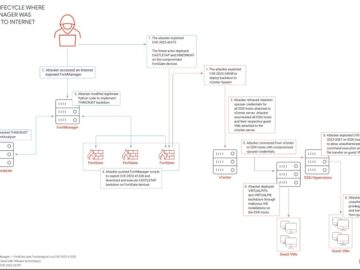
After unearthing a malware campaign targeting ESXi hypervisors two years ago, researchers have now revealed extensive details into their investigation…
Car dealership software-as-a-service provider CDK Global was hit by a massive cyberattack, causing the company to shut down its systems…
Two young men, Sagar Steven Singh (20) aka Weep and Nicholas Ceraolo (26) aka Ominous and Convict hailing from New…
Threat actors don’t just seek out security weaknesses. They look for situational vulnerabilities. Every holiday season, for instance, they come…
Software is the heart of our connected world, but as its importance grows, so do cyber threats. According to the…
Jun 19, 2024NewsroomCybercrime / Crypto Security Crypto exchange Kraken revealed that an unnamed security researcher exploited an “extremely critical” zero-day…
Generative AI has the potential to make social engineering attacks much more sophisticated and personalised. The technology can rapidly mine…
Google has announced a new update for the Chrome browser, rolling out version 126.0.6478.114/115 for Windows and Mac and 126.0.6478.114…