Hackers are offering “free” mobile data access on Telegram channels by exploiting loopholes in telecom provider policies, which target users…
Jun 19, 2024NewsroomCybercrime / Cryptocurrency A threat actor who goes by alias markopolo has been identified as behind a large-scale…
Several phishing campaign kits have been used widely by threat actors in the past. One popular PhaaS (Phishing-as-a-Platform) was Caffeine,…
Jun 19, 2024The Hacker NewsGDPR Compliance / Data Privacy Are your tags really safe with Google Tag Manager? If you’ve…
Google has released a critical security update for its Chrome browser, addressing six high-severity vulnerabilities that could potentially lead to…
The notorious IntelBroker hacker, who has previously been linked to high-profile breaches of major companies and government entities, has claimed…
Cryptocurrency users are being targeted with legitimate-looking but fake apps that deliver information-stealing malware instead, Recorder Future’s researchers are warning….
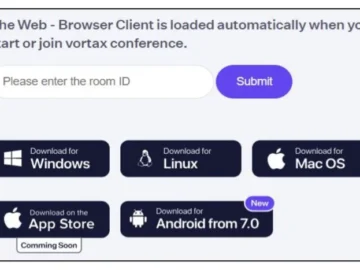
Jun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne…
Maxicare, one of the leading health maintenance organizations, has reported a security incident involving unauthorized access to personal information. The…
Researchers have developed a real-time browser extension integrated with machine learning algorithms to detect phishing websites with remarkable accuracy. This…
In late March, a Taiwanese data analyst posted on social media about an odd satellite image: It appeared that the…
Titania, specialists in continuous network security and compliance assurance solutions, announced the release of compelling new research that highlights a…