Google Chrome users worldwide are being warned about a targeted cyber attack specifically aimed at Android browsers across various devices….
In the realm of IT and cybersecurity, businesses often face the daunting task of preparing for and responding to potential…
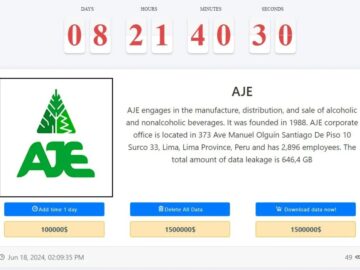
AJE Group, a prominent company in the manufacture, distribution, and sale of alcoholic and nonalcoholic beverages, has allegedly fallen victim…
This article compiles excerpts from various reports, presenting statistics and insights on cybersecurity threats faced by businesses and individuals alike….
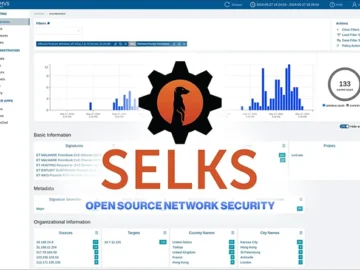
SELKS is a free, open-source, turnkey solution for Suricata-based network intrusion detection and protection (IDS/IPS), network security monitoring (NSM), and…
Application Penetration Tester ShiftCode Analytics | USA | On-site – View job details As an Application Penetration Tester, you will…
Action1 researchers found an alarming increase in the total number of vulnerabilities across all enterprise software categories. “With the NVD’s…
Two Rhode Island men pleaded guilty to hacking into a confidential federal law enforcement database and using the sensitive information…
Medibank or its partners allegedly missed or didn’t act on alerts from its endpoint detection and response (EDR) tool before…
Microsoft has confirmed that Windows 10 apps will mistakenly display an “How do you want to open this file?” dialog…
Federal Treasury lawyers are having to rely on SharePoint and Excel to source knowledge and precedents for their “increasing volume” of…
Microsoft has confirmed that Windows 10 apps will mistakenly display an “How do you want to open this file?” dialog…