Researchers from Cyble Research and Intelligence Labs (CRIL) have discovered a QR code-based phishing campaign that uses malicious Word documents…
NHS Dumfries and Galloway health authorities have warned that confidential patient data from its systems had been accessed and copied…
A US judge rejected Meta Platforms’ bid to dismiss a lawsuit by billionaire Australian mining magnate Andrew Forrest over scam…
AMD is investigating whether it suffered a cyberattack after a threat actor put allegedly stolen data up for sale on…
Nvidia has become the world’s most valuable company, dethroning tech heavyweight Microsoft as its high-end processors play a central role…
A new phishing-as-a-service (PhaaS) platform called ONNX Store is targeting Microsoft 365 accounts for employees at financial firms using QR…
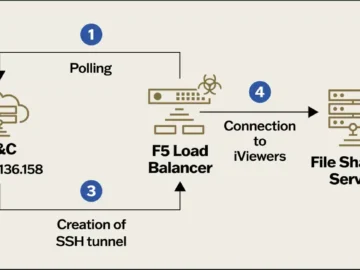
Researchers that were called to investigate a cyberattack on a large organization in late 2023 have traced the activity to…
VMware has issued a security advisory addressing critical vulnerabilities in vCenter Server, including remote code execution and local privilege escalation flaws….
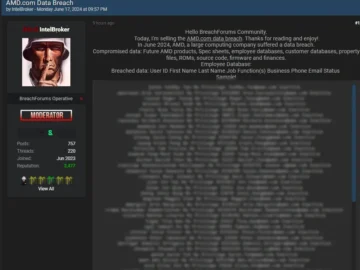
The notorious threat actor known as Intelbroker claims to have orchestrated a massive data breach of AMD, a top player…
A scathing report by Australia’s Information Commissioner details how misconfigurations and missed alerts allowed a hacker to breach Medibank and steal…
Sometimes you’ll see the term “overlays” used in articles about malware and you might wonder what they are. In this…
Experts slammed the latest European Union proposals for chat control to prevent child sexual abuse calling it a front face…