Jun 24, 2024NewsroomVulnerability / Artificial Intelligence Google has developed a new framework called Project Naptime that it says enables a…
Lindex Group, an international retail giant specializing in high-quality fashion, has reportedly fallen victim to a data breach. According to…
In 2024, Google reported that less than 1% of Chrome Web Store installations contained malware. Extensions are small software programs…
Jun 24, 2024NewsroomArtificial Intelligence / Cloud Security Cybersecurity researchers have detailed a now-patch security flaw affecting the Ollama open-source artificial…
What follows is based on our combined experience of around 52 years of legal advice to the IT and outsourcing…
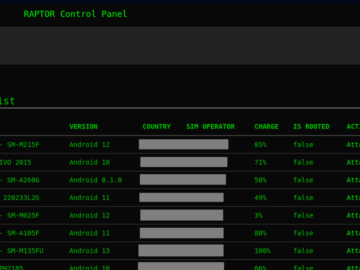
Experts observed approximately 120 malicious campaigns using the Rafel RAT Pierluigi Paganini June 24, 2024 Multiple threat actors are using…
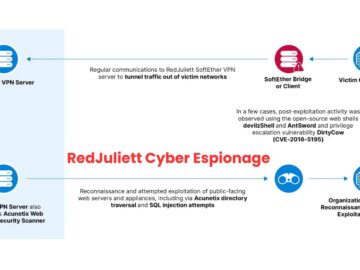
A suspected Chinese state-sponsored cyberespionage group, RedJuliett, targeted the Taiwanese government and academic, technological, and diplomatic organizations between November 2023…
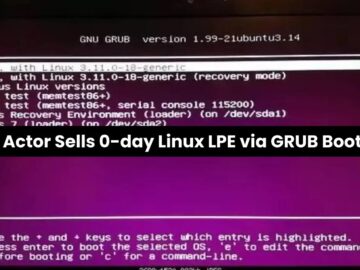
A new threat actor has emerged, claiming a zero-day vulnerability in the Linux GRUB bootloader that allows for local privilege…
24 Jun 5 Of The Highest-Paying Cybersecurity Jobs Right Now Posted at 08:53h in Blogs by Di Freeze This week…
Buckinghamshire Council has deployed Copilot for Microsoft 365 to improve operational efficiency. By using Microsoft’s artificial intelligence (AI) tool, the…
Levi Strauss & Co., a renowned American clothing company, has disclosed a significant data breach affecting over 72,000 customers. The…
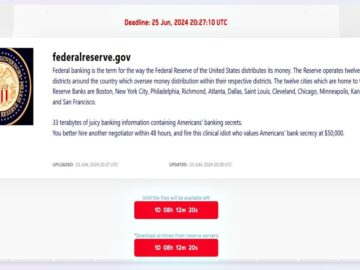
The notorious LockBit ransomware gang claims to have breached the Federal Reserve Board (Federalreserve.gov), the central banking system of the…