Cybersecurity Architect Alstom | France | On-site – View job details As a Cybersecurity Architect, you will analyze solutions, identify…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Google’s artificial intelligence (AI)-powered cybersecurity agent called Big Sleep has been credited by…
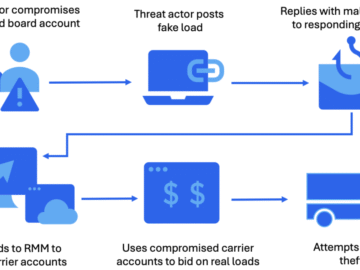
Crooks exploit RMM software to hijack trucking firms and steal cargo Pierluigi Paganini November 04, 2025 Hackers target trucking firms…
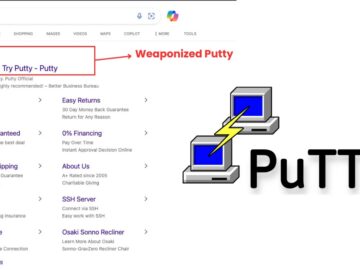
Looks can be deceiving, so much so that the familiar icon could mask malware designed to steal your data and…
An ongoing malicious advertising campaign is weaponizing legitimate software downloads to deploy OysterLoader malware, previously identified as Broomstick and CleanUpLoader….
Microsoft has acknowledged a critical issue affecting Windows Server 2025 systems enrolled in the Hotpatch program. A recent Windows Server…
In this Help Net Security interview, Dr. Bernhards Blumbergs, Lead Cyber Security Expert at CERT.LV, discusses how cyberspace has become…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Malware Microsoft has disclosed details of a novel backdoor dubbed SesameOp that uses OpenAI…
Company leaders need to recognize the gravity of cyber risk, turn awareness into action, and put security front and center…
The Rhysida ransomware gang has been running a sophisticated malvertising campaign that delivers OysterLoader malware through deceptive search engine advertisements,…
The days when YouTube was just a place for funny clips and music videos are behind us. With 2.53 billion…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Malware Microsoft has disclosed details of a novel backdoor dubbed SesameOp that uses OpenAI…