Pure Storage makes a big deal of its subscription models of purchasing for storage hardware. It believes it can offer…
Researchers at SonarCloud have discovered critical security vulnerabilities in Mailcow, a popular open-source email server solution, that could have allowed…
The open-source Rafel RAT is being leveraged by multiple threat actors to compromise Android devices and, in some cases, to…
Jun 24, 2024The Hacker NewsThreat Intelligence / Cybersecurity Learn about critical threats that can impact your organization and the bad…
The Sellafield nuclear waste site has pleaded guilty to criminal charges brought by the industry regulator, admitting to significant cyber…
Yana Li, Director of IT & Platform Security at WebBeds, embodies resilience, determination, and a passion for cybersecurity that has…
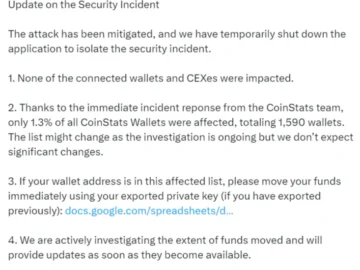
Crypto portfolio tracking app Coinstats has found itself at the center of a security breach, impacting approximately 1,590 user wallets….
Cybersecurity experts have discovered a critical flaw in Apple’s latest augmented reality (AR) headset, the Apple Vision Pro. This vulnerability…
In today’s digital age, staying informed about the latest developments in cybersecurity is crucial. Cyber threats are constantly evolving, and…
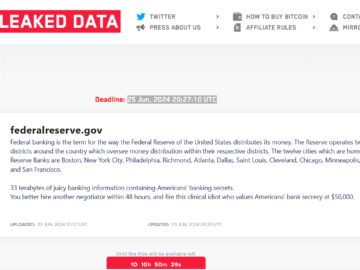
LockBit claims the hack of the US Federal Reserve Pierluigi Paganini June 24, 2024 The Lockbit ransomware group announced that…
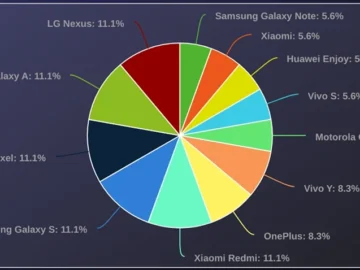
Android has many features and access to apps but is prone to security risks due to its open-source nature. Android…
A vulnerability in Microsoft Power BI allows unauthorized users to access sensitive data underlying reports, which affects tens of thousands…