“I can tell you with complete confidence that ransomware attacks harm patients,” says Hannah Neprash, an associate professor of health…
Jun 24, 2024NewsroomCyber Espionage / Hacking A likely China-linked state-sponsored threat actor has been linked to a cyber espionage campaign…
A former Post Office investigator who deleted information from an expert IT witness statement during the wrongful prosecution of a…
Jollibee Foods Corporation (JFC), which is the largest fast-food chain operator in Philippines, has launched an investigation for an alleged…
The Handala hacker group has claimed responsibility for breaching Zerto, an Israeli firm specializing in critical cybersecurity services. The Zerto…
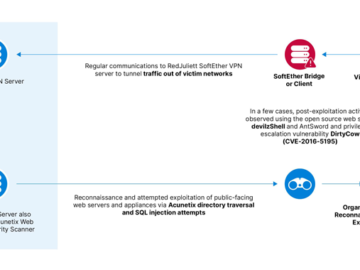
ExCobalt Cybercrime group targets Russian organizations in multiple sectors Pierluigi Paganini June 24, 2024 The cybercrime group ExCobalt targeted Russian…
UnitedHealth has, for the first time, detailed the types of medical and patient data stolen in the extensive cyberattack on…
A new vulnerability, CVE-2024-29973, has been discovered in Zyxel NAS devices, exposing them to attacks from a Mirai-like botnet. This…
June 21, 2024 – A cybercriminals is giving 1 million data records from the Ticketmaster breach away for free, saying…
Two consulting companies, Guidehouse Inc. and Nan McKay and Associates, have agreed to pay $11.3 million to resolve allegations of…
The Qilin ransomware group, responsible for the recent attack on NHS, resulting in the cancellation of nearly 1200 operations and…
ECU Worldwide, a global player in Less than Container Load (LCL) consolidation, has appointed Rajneesh Garg as its new Chief…