A critical security vulnerability, CVE-2024-5806, has been identified in MOVEit Transfer, a widely used managed file transfer software. The vulnerability poses significant risks to…
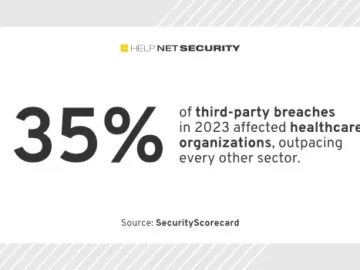
While the healthcare sector gets a “B+” security rating for the first half of 2024, it faces a critical vulnerability:…
Jun 26, 2024NewsroomSupply Chain Attack / Web Security Google has taken steps to block ads for e-commerce sites that use…
Australian banks and organisations exploited by SMS scammers, and the telcos asked to filter and block scams, want a mandatory…
CISO Influx | Indonesia | Remote – View job details As a CISO, you will be responsible for protecting Influx…
The data you’ve worked hard to secure is facing more threats than ever, and for more reasons than you realise,…
Progress Software’s popular MOVEit Transfer and MOVEit Cloud-managed, file transfer solutions, have been found to contain a critical authentication bypass…
In this Help Net Security interview, Morgan Wright, Chief Security Advisor at SentinelOne, discusses how AI is utilized in modern…
The National Health Laboratory Service (NHLS), South Africa’s primary diagnostic pathology service for public healthcare facilities, has fallen victim to…
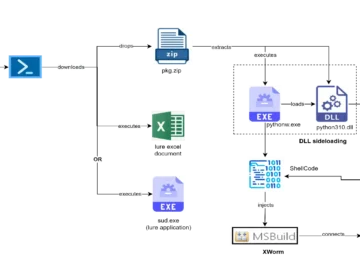
Cyble Research and Intelligence Labs (CRIL) researchers have observed the Russia-linked threat actor group UAC-0184 targeting Ukraine with the XWorm…
Domino’s Pizza Enterprises is set to lose its group chief operating officer – whose remit covers group IT, digital, data,…
By Vira Shynkaruk, Cybersecurity Content Expert, UnderDefense Making the right call on cybersecurity solutions is paramount for businesses, especially now,…