Exploring the Dark Web: Essential Insights Revealed By Elena Thomas, Digital Content Strategist, SafeAeon Inc. The internet is like a…
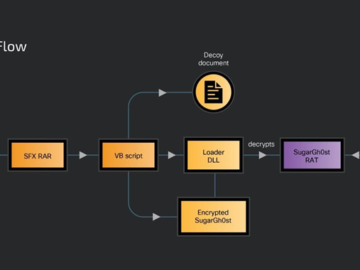
Jun 21, 2024NewsroomMalware / Threat Intelligence A previously undocumented Chinese-speaking threat actor codenamed SneakyChef has been linked to an espionage…
Ransomware gang Qilin has published almost 400GB of sensitive healthcare data online following its high-profile malware attack on pathology laboratory…
The Tor Project has released Tor Browser 13.5, bringing several improvements and enhancements for Android and desktop versions. The Tor Browser…
Two critical vulnerabilities have been discovered in NVIDIA’s Triton Inference Server, a widely used AI inference server. These vulnerabilities, CVE-2024-0087…
CDK Global has disclosed that it experienced an additional cyberattack in the course of its investigation into a cyberattack that…
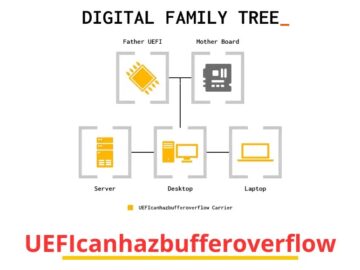
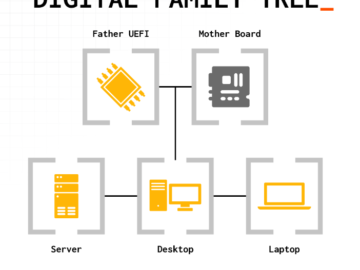
The Phoenix SecureCore UEFI firmware has discovered a new vulnerability, which runs on several Intel Core Desktop and mobile processors….
Jun 21, 2024NewsroomPhishing Attack / Email Security Cybersecurity researchers have shed light on a new phishing campaign that has been…
With artificial intelligence (AI) the recurring theme of the Domino Data RevX 2024 London event that took place on 13…
Among the diverse array of Android malware available on the dark web markets, Rafel RAT stands out as a particularly…
UEFICANHAZBUFFEROVERFLOW flaw in Phoenix SecureCore UEFI firmware potentially impacts hundreds of PC and server models Pierluigi Paganini June 21, 2024…
Hackers often attack ESXi systems, as they are widely used in enterprise environments to manage virtualized infrastructure, making them lucrative…