A recent rise in data breaches from illegal Chinese OTT platforms exposes that user information, including names and financial details,…
A moderator of the notorious data breach trading platform BreachForums is offering data for sale they claim comes from a…
In the latest update of “Secure by Design”, the Cybersecurity and Infrastructure Security Agency (CISA) highlighted the critical importance of…
Researchers discovered a new malware loader named SquidLoader targeting Chinese organizations, which arrives as an executable disguised as a Word…
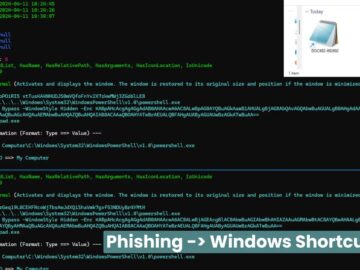
LNK files, a shortcut file type in Windows OS, provide easy access to programs, folders, or websites. Created automatically during…
Normal0 falsefalsefalse EN-US /* Style Definitions */table.MsoNormalTable{mso-style-name:”Table Normal”;mso-tstyle-rowband-size:0;mso-tstyle-colband-size:0;mso-style-noshow:yes;mso-style-priority:99;mso-style-parent:””;mso-padding-alt:0in 5.4pt 0in 5.4pt;mso-para-margin:0in;mso-pagination:widow-orphan;mso-hyphenate:none;font-size:10.0pt;mso-bidi-font-size:11.0pt;font-family:”Calibri”,sans-serif;mso-ascii-font-family:Calibri;mso-ascii-theme-font:minor-latin;mso-hansi-font-family:Calibri;mso-hansi-theme-font:minor-latin;mso-bidi-font-family:Calibri;mso-bidi-theme-font:minor-bidi;mso-font-kerning:1.0pt;mso-ligatures:standardcontextual;} The United States government has imposed a ban on…
In today’s digital age, where email communication is integral to business operations, the threat of Business Email Compromise (BEC) looms…
Cyber A.I. Group, Inc., an early stage cybersecurity, A.I. and IT services company, announced today the engagement of Walter L….
Cyber A.I. Group, Inc., an early stage cybersecurity, A.I. and IT services company, announced today the engagement of Walter L….
Jun 21, 2024NewsroomSoftware Security / Threat Intelligence The U.S. Department of Commerce’s Bureau of Industry and Security (BIS) on Thursday…
A Panaseer investigation into organizations’ annual 10-K filings reported to the SEC shows that from January-May 2024, at least 1,327…
Cilium is an open-source, cloud-native solution that leverages eBPF technology in the Linux kernel to provide, secure, and monitor network…