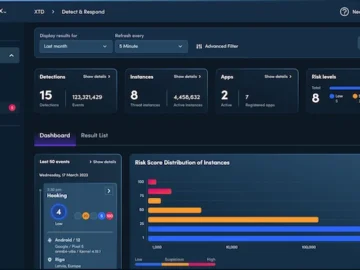
Verimatrix announced major enhancements to its XTD dashboard, providing customers with better visibility into application security risks and more actionable…
The Post Office’s relationship with IT supplier Fujitsu was “tense” in 2010 amid major problems rolling out the online version…
The European Union has introduced two critical regulatory frameworks: the Network and Information Security (NIS) Directive and the Digital Operational…
Fortra has issued a critical security advisory regarding a hard-coded password vulnerability in its FileCatalyst software, explicitly affecting the TransferAgent…
Threat actors leverage meeting software applications and tools to penetrate weak security loopholes, infiltrate secure settings and organizations, steal highly…
Threat actors exploit Linux systems because they are prevalent in organizations that host servers, databases, and other important resources. Exploiting…
Jun 20, 2024NewsroomMalware / Cyber Attack Cybersecurity researchers have uncovered a new evasive malware loader named SquidLoader that spreads via…
CDK Global, a provider of software solutions to auto dealerships across the United States, has fallen victim to a significant…
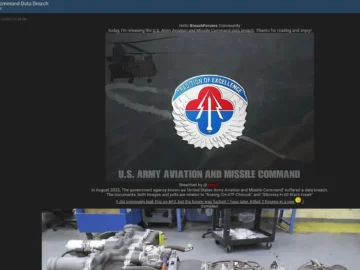
The U.S. Army Aviation and Missile Command (AMCOM), based at Redstone Arsenal, Alabama, has been spotlighted following an alleged data…
1.) Recently, the Qilin ransomware group, believed to originate from Russia, targeted three hospitals and a network, severely disrupting emergency…
Password security has seen dramatic shifts driven by the escalation of cyber threats and technological advancements. This eBook covers: Best…
Organizations have made progress in the past 12 months related to advancing their OT security posture, but there are still…