The notorious IntelBroker hacker, who has previously been linked to high-profile breaches of major companies and government entities, has claimed…
Cryptocurrency users are being targeted with legitimate-looking but fake apps that deliver information-stealing malware instead, Recorder Future’s researchers are warning….
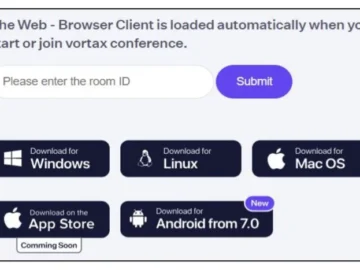
Jun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne…
Maxicare, one of the leading health maintenance organizations, has reported a security incident involving unauthorized access to personal information. The…
Researchers have developed a real-time browser extension integrated with machine learning algorithms to detect phishing websites with remarkable accuracy. This…
In late March, a Taiwanese data analyst posted on social media about an odd satellite image: It appeared that the…
Titania, specialists in continuous network security and compliance assurance solutions, announced the release of compelling new research that highlights a…
Hackers exploit the Windows BitLocker tool, as this utility offers a very powerful tool for selectively encrypting access to the…
Cybersecurity firm Sygnia has discovered a sophisticated cyberespionage campaign allegedly linked to China. Their research shared with Hackread.com ahead of…
Independent forensic accountants contracted to investigate controversial Post Office Horizon system in 2012 describe Post Office cover-ups, threats, obstruction and…
ANZ Plus customers will be able to reuse their banking identity with certain merchants and businesses via the ConnectID service….
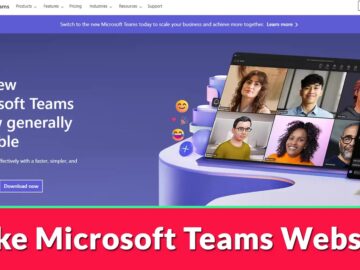
Fake websites of authoritative and popular companies claiming to be genuine sites make users believe that the site belongs to…