A critical Exim vulnerability in the widely-used Exim mail transfer agent (MTA) has recently been disclosed, potentially affecting over 1.5…
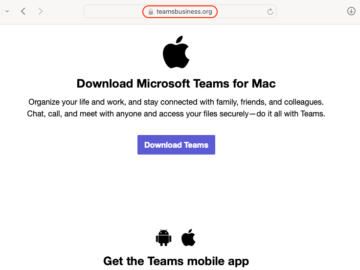
A sophisticated malvertising campaign is targeting Mac users searching for Microsoft Teams, highlighting the growing competition among malware creators in…
Australia plans to introduce a law by the end of the year forcing internet companies to proactively stop hosting scams…
Critical flaw in Exim MTA could allow to deliver malware to users’ inboxes Pierluigi Paganini July 12, 2024 A critical…
Pharmacy giant Rite Aid confirmed a data breach after suffering a cyberattack in June, which was claimed by the RansomHub…
AT&T, one of the largest telecommunications companies in the United States, has disclosed a significant data breach that exposed the…
AT&T Corp. disclosed today that a new data breach has exposed phone call and text message records for roughly 110…
But that’s not all. Each week, we round up the security news we didn’t cover in depth ourselves. Click on…
mSpy, a widely used phone spyware application, has suffered a significant data breach, exposing the sensitive information of millions of…
DeFi apps on Squarespace are vulnerable to a DNS hijacking attack that redirects users to malicious sites. Over 120 DeFi…
On June 3, the public comment period closed for the U.S. Cybersecurity & Infrastructure Security Agency’s (CISA) Notice of Proposed…
12 Jul The Future Of Cybersecurity: Emerging Threats And How To Combat Them Posted at 09:42h in Blogs by Di…