Whenever a company is notified about or discovers a critical flaw in their system/application that has the potential to be…
Two men have been charged in a Chicago federal court for operating “Empire Market,” a dark web marketplace that facilitated…
A team of Stanford graduates developed Pi Coin, which has been generating significant buzz in the cryptocurrency community. Unlike many…
The Northern Territory’s Department of Corporate and Digital Development (DCDD) has appointed Bruno Braga as the new executive director of…
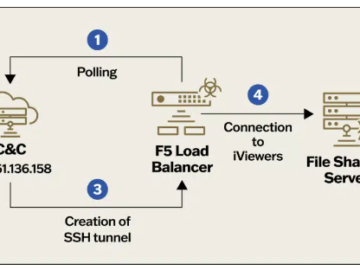
China-linked Velvet Ant uses F5 BIG-IP malware in cyber espionage campaign Pierluigi Paganini June 17, 2024 Chinese cyberespionage group Velvet…
Panera Bread, an American chain of fast food restaurants, most likely paid a ransom after being hit by a ransomware…
By Hoda Alkhzaimi The technological prowess of small nations is increasingly recognized as a significant driver of global economic power….
By: Abhilash R., Head of Cybersecurity at OQ Trading In a progressively digital world, small and medium sized enterprises (SMEs)…
I’m working on my context.md file for my personal Digital Assistant, and one part of that will be my model.md…
A group of suspected Chinese cyberespionage actors named ‘Velvet Ant’ are deploying custom malware on F5 BIG-IP appliances to gain…
With companies coming forward every day announcing impacts from their third-party cloud data storage vendor, the Snowflake data breach seems…
Cybersecurity researchers at Kaspersky Lab have uncovered 24 vulnerabilities within biometric access systems manufactured by ZKTeco, a major Chinese provider….