Researchers have developed a real-time browser extension integrated with machine learning algorithms to detect phishing websites with remarkable accuracy. This…
In late March, a Taiwanese data analyst posted on social media about an odd satellite image: It appeared that the…
Titania, specialists in continuous network security and compliance assurance solutions, announced the release of compelling new research that highlights a…
Hackers exploit the Windows BitLocker tool, as this utility offers a very powerful tool for selectively encrypting access to the…
Cybersecurity firm Sygnia has discovered a sophisticated cyberespionage campaign allegedly linked to China. Their research shared with Hackread.com ahead of…
Independent forensic accountants contracted to investigate controversial Post Office Horizon system in 2012 describe Post Office cover-ups, threats, obstruction and…
ANZ Plus customers will be able to reuse their banking identity with certain merchants and businesses via the ConnectID service….
Fake websites of authoritative and popular companies claiming to be genuine sites make users believe that the site belongs to…
An Irish hacker, who was involved in cyberattacks at the age of 13, has now walked free from court after…
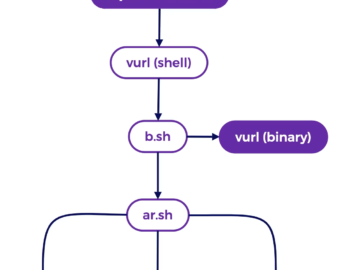
Cryptojacking campaign targets exposed Docker APIs Pierluigi Paganini June 19, 2024 A malware campaign targets publicly exposed Docker API endpoints…
Managing cybersecurity for any organization is no easy feat. Improving cybersecurity maturity is often even more difficult, made increasingly challenging…
Jun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that…