As organizations in the healthcare sector continue to be a prime target for ransomware gangs and CISA warns about a…
The Police Service of Northern Ireland (PSNI) is bracing for a hefty £750,000 fine following last year’s data breach. The…
The First Nations Health Authority (FNHA) in British Columbia is currently grappling with the aftermath of a recent cyberattack on…
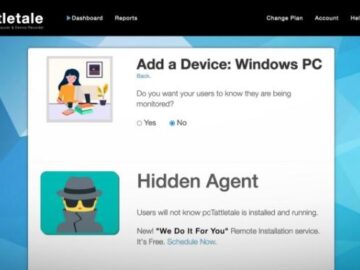
A consumer-grade spyware app found in check-in systems of 3 US hotels Pierluigi Paganini May 23, 2024 A researcher discovered…
LastPass, a widely used password manager trusted by millions of consumers and businesses globally, has announced an upgrade to its…
Microsoft has shifted its scripting options for web development and task automation. The company is replacing VBScript with more advanced…
File Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps…
Microsoft has officially announced the gradual deprecation of VBScript, with plans to replace it with more advanced alternatives such as…
Rockwell Automation Urges Caution Regarding Industrial Control Systems Rockwell Automation, a leading provider of industrial control systems (ICS), has issued…
In this Help Net Security, Prakash Mana, CEO at Cloudbrink, discusses the primary challenges companies face when transitioning to a…
May 23, 2024NewsroomEndpoint Security / Data Privacy Microsoft on Wednesday outlined its plans to deprecate Visual Basic Script (VBScript) in…
Optus will face Federal Court action over its 2022 data breach, with the Australian Communications and Media Authority filing paperwork…