Organizations have been doing backup and recovery for decades and many feel that they have reactive data protection under control….
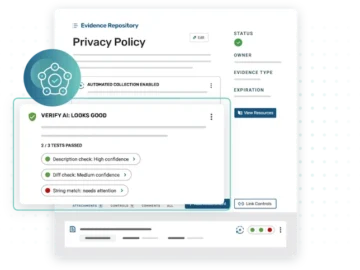
Strike Graph launches VerifyAI, an innovative AI-powered technology for intelligent testing that goes beyond basic security control automation to understand…
Organisations are increasingly turning to algorithms to manage and evaluate various aspects of work. This form of algorithmic management can…
Cybersecurity researchers uncovered a sophisticated cryptojacking campaign that leverages vulnerable drivers to disable well-known security solutions, thereby evading detection. This…
An ongoing malware campaign exploits Microsoft Exchange Server flaws Pierluigi Paganini May 22, 2024 A threat actor is targeting organizations…
AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced today that its proprietary search engine, Criminal IP, is…
In 2020, Tesla even wrote in a filing to the US Federal Communications Commission that it would be implementing ultra-wideband…
Torrance, United States / California, May 22nd, 2024, CyberNewsWire AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced…
The recent WebTPA data breach has impacted approximately 2.4 million individuals, with unauthorized access to a network server leading to…
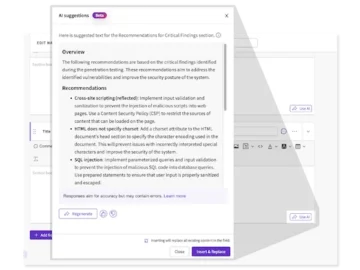
PlexTrac announced Plex AI, the company’s AI-powered offensive security report writing tool, real-time team collaboration to enable simultaneous report editing…
Working with wild gorillas and rescue gibbons isn’t the traditional route into a career in data and technology. But for…
A previously unknown threat actor dubbed “Unfading Sea Haze” has been targeting military and government entities in the South China…