By Kimberly Sutherland, vice president, fraud and identity strategy, LexisNexis® Risk Solutions Digital fraud has seen a substantial increase in…
Zoom Meetings now offer post-quantum end-to-end encryption, safeguarding your confidential conversations even from the potential threat of quantum computers. This…
22 May Privacy Pandemic: How Cybercriminals Determine Targets, Attack Identities, And Violate Privacy Posted at 09:00h in Blogs by Di…
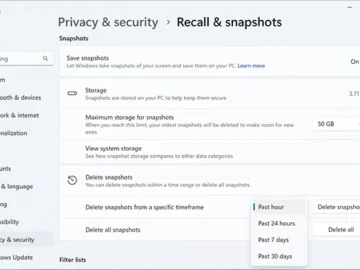
Microsoft has announced the Copilot+ line of Windows 11-powered PCs that, among other things, will have Recall, a feature that…
May 22, 2024NewsroomICS Security / Vulnerability Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not…
The Crown Commercial Service (CCS) is accused of sending mixed messages to non-UK-based cloud service providers that want to participate…
Mid-tier firms in India’s $254 billion ($382 billion) information technology sector took market share from industry goliaths in recent quarters…
Security researcher Meowmycks unveiled a new tool named LetMeowIn, designed to harvest credentials from the Local Security Authority Subsystem Service…
Infinidat has added two HDD and flash storage array products – dubbed Infinibox G4 – that claim a 2x performance…
Thousands of GitHub Enterprise Server (GHES) instances in the United States using SAML single sign-on (SSO) authentication are at high…
A phishing email with a malicious zip attachment initiates the attack. The zip contains a single executable disguised as an…
New York City, May 22 – Solv Protocol, a unified yield and liquidity layer for major digital assets, has surpassed…