OmniVision Technologies, Inc. (OVT) recently disclosed a significant security breach that compromised its clients’ personal data. The company, known for…
Since the first edition of The Ultimate SaaS Security Posture Management (SSPM) Checklist was released three years ago, the corporate…
During the ServiceNow Knowledge24 user conference in Vegas, actress, author and producer Viola Davis said: “I did not start with a…
Critical GitHub Enterprise Server Authentication Bypass bug. Fix it now! Pierluigi Paganini May 22, 2024 GitHub addressed a vulnerability in…
The U.S. Environmental Protection Agency (EPA) has sent an enforcement warning about the serious cyber threats and holes in community…
Blended learning, a method that melds in-person teaching with online learning, has become increasingly popular recently. This innovative educational approach…
Veeam has patched four vulnerabilities in Backup Enterprise Manager (VBEM), one of which (CVE-2024-29849) may allow attackers to bypass authentication…
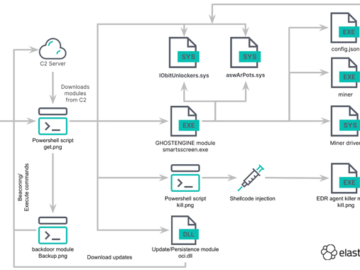
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart…
Bug bounty programs are a pivotal tool in the cybersecurity landscape, offering a win-win situation for organizations looking to boost…
Multiple vulnerabilities involving SQL injection have been identified in Ivanti Endpoint Manager. These vulnerabilities could potentially enable malicious actors to…
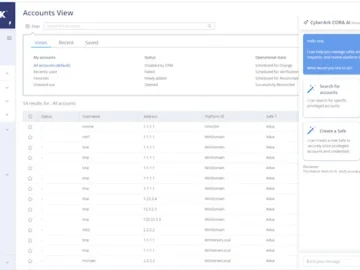
CyberArk announced CyberArk CORA AI, a new set of AI-powered capabilities that will be embedded across its identity security platform….
The CyberNiggers hacker group plans to set up a new web domain of their own after they lost the ability…