At its annual re:Inforce conference, Amazon Web Services (AWS) has announced new and enhanced security features and tools. Additional multi-factor…
Following days of user pushback that included allegations of forcing a “spyware-like” Terms of Service (ToS) update into its products,…
(ROracle shares jumped nine percent as investors cheered a boom in demand for the company’s relatively low-cost cloud infrastructure services…
Microsoft has announced that the DirectAccess remote access solution is now deprecated and will be removed in a future release…
Hackers go for Apple due to its massive user base along with rich customers, including business people and managers who…
Cybercriminals continue to attack enterprises and federal and state institutions by using sophisticated tools and adopting new breaching methods. Global…
Consumers’ eagerness to consume content, and fickleness as to where they consume it, has led to the rise of the…
A resident of Moreton Bay, Australia was shocked to discover that the private information of several resident ratepayers in the…
On stage this week, CEO Tim Cook’s Apple announced a splashy deal with OpenAI to include its powerful artificial intelligence…
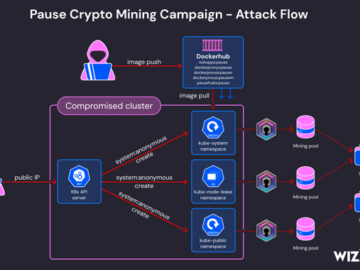
Jun 12, 2024NewsroomKubernetes / Endpoint Security Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to…
The Ukraine cyber police have arrested a 28-year-old Russian man in Kyiv for working with Conti and LockBit ransomware operations to…
Mozilla has released Firefox 127, addressing 15 security vulnerabilities, some of which have been rated as high impact. This update…