Kaiser Permanente, one of the largest healthcare providers in the United States, was the victim of a cyber attack that…
The Federal Communications Commission has fined the largest phone carriers in the country – AT&T, Sprint, T-Mobile and Verizon –…
Jareh Sebastian Dalke, 32, of Colorado Springs, was sentenced today to 262 months in prison for attempted espionage in connection…
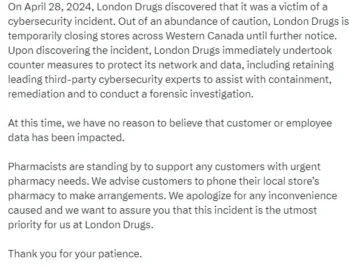
Retail and pharmacy chain London Drugs has announced the closure of its stores across Western Canada after falling victim to…
NCSC: New UK law bans default passwords on smart devices Pierluigi Paganini April 30, 2024 The UK National Cyber Security…
In a significant update from the Linux kernel’s security team, a critical vulnerability identified as CVE-2024-26925 has been addressed to…
In the world of cloud computing, Amazon Web Services (AWS) is a giant that offers a wide range of services…
Apr 30, 2024NewsroomIoT Security / Botnet The U.K. National Cyber Security Centre (NCSC) is calling on manufacturers of smart devices…
The Saline Water Conversion Corporation of Saudi Arabia became the target of a Distributed Denial of Service (DDoS) attack allegedly…
AWS Customer Faces Massive Bill Due to Open-Source Tool Misconfiguration. In a startling incident, an AWS customer faced a staggering…
Gemini 1.5 Pro is the latest version of the Gemini AI malware analysis platform, which is set to transform the…
Security industry leaders believe that AI and automation technologies are critical to addressing the complexities of modern security operations, according…