Cybersecurity experts have meticulously traced the timeline of a sophisticated ransomware attack that spanned 29 days from the initial breach…
The Product Security and Telecommunications Infrastructure (PSTI) Act has come into effect today, requiring manufacturers of consumer-grade IoT products sold…
Apr 29, 2024NewsroomDNS Security / Cyber Espionage A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated…
Hacktivists claimed breaching the network of Belarusian intelligence agency and allegedly leaked their data in response to the intelligence chief’s…
Financial Business and Consumer Solutions (FBCS) data breach impacted 2M individuals Pierluigi Paganini April 29, 2024 Financial Business and Consumer…
Every organization has its strategy of alerting and on-call. The experience of being on-call in different teams for different stacks…
To outmanoeuvre cybercriminals, the key is to beat them to the punch by working with ethical hackers. However, a question…
The popular open-source platform Grafana, widely used for monitoring and observability, has been found to contain a severe SQL injection…
29 Apr How A Cryptocurrency Investor Lost $200K To A Pig Butchering Scam, Fights Back Posted at 09:36h in Blogs…
Hedgey Finance, a prominent token infrastructure platform, has reported a massive theft of approximately $44.5 million in cryptocurrencies. This incident…
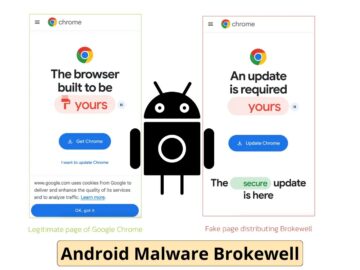
A new family of mobile malware known as “Brokewell” has been found to have a wide range of device takeover…
Datacentre energy consumption and operational efficiency are under intense scrutiny. Sensing a need to control datacentre growth, legislators and regulators…