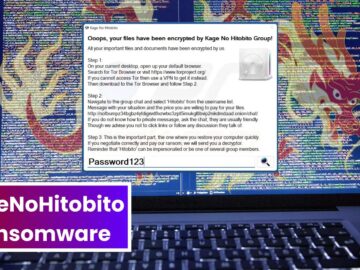
A new ransomware named KageNoHitobito has been targeting Windows users across various countries. It encrypts their data and demands a…
Multiple Brocade SANnav SAN Management SW flaws allow device compromise Pierluigi Paganini April 29, 2024 Multiple flaws in Brocade SANnav…
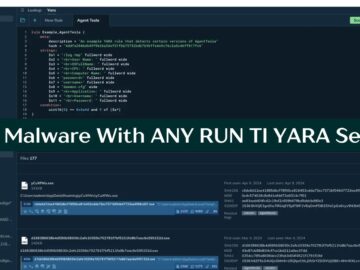
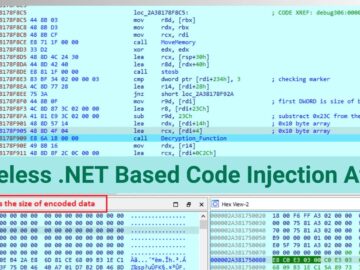
YARA is a rule-based malware detection tool that utilizes regular expressions and textual/binary signatures to create descriptions (rules) for identifying…
Okta has issued a warning about the increasing prevalence of credential-stuffing attacks. These attacks, which leverage stolen user credentials to…
April 24, 2024 – The US Senate has approved a bill that will ban TikTok, unless it finds a new…
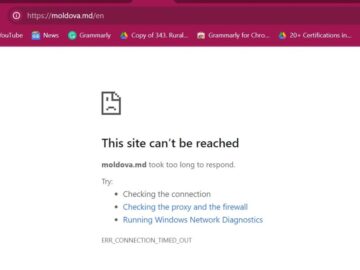
The notorious NoName ransomware group this time has allegedly set its sights on Moldova, targeting key government websites in what…
A recent malware campaign used a VBA macro in a Word document to download and execute a 64-bit Rust binary….
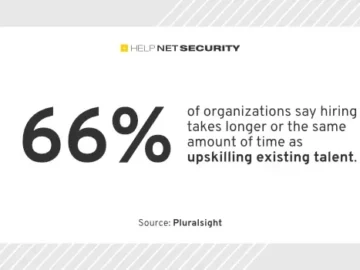
The list of skills technologists and organizations need to succeed grows with each new tech advancement, according to Pluralsight. But…
Researchers discovered a vulnerability in an archived Apache project, highlighting the risk of using outdated third-party dependencies, where attackers can…
Prompt Fuzzer is an open-source tool that evaluates the security of your GenAI application’s system prompt against dynamic LLM-based threats….
Most businesses see offensive AI fast becoming a standard tool for cybercriminals, with 93% of security leaders expecting to face…
I said goodbye to the frustrations of Beehiiv’s built-in search and now enjoy a much more efficient and user-friendly experience….