Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Hackers backdoored Cisco ASA devices…
Hackers have honed in on a critical WP-Automatic plugin vulnerability, aiming to infiltrate WordPress websites by creating unauthorized admin accounts, according…
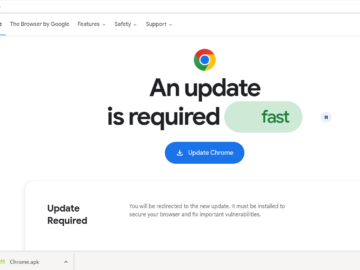
CRIL Researchers observed a new android banking trojan ‘Brokewell,’ being distributed through a phishing site disguised as the official Chrome…
Image: AI-generated via Midjourney Japanese police placed dummy payment cards in convenience stores to protect the elderly targeted by tech…
Hackers may have accessed thousands of accounts on the California state welfare platform Pierluigi Paganini April 27, 2024 Threat actors…
This week’s TCE Cyberwatch delves into a range of pressing cybersecurity issues impacting the world today. From the rise of…
Okta warns of an “unprecedented” spike in credential stuffing attacks targeting its identity and access management solutions, with some customer…
By Roman Faithfull, Cyber Intelligence Lead, Cyjax 2024 will see more elections than any other year in history: the UK,…
By Lakshmi Mittra, SVP and Head, Clover Academy In the rapidly changing and dynamic tech environment of today, future-proofing the…
Apr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging…
By Dwayne McDaniel, GitGuardian Developer and Security Advocate, GitGuardian The modern world of DevOps means relying on our code connecting…
27 Apr Protecting Real Estate Professionals From Ransomware Posted at 08:24h in Blogs by Di Freeze This week in cybersecurity…