Electronic health records (EHRs) have become crucial tools for storing and managing patient information. These digital records contain a wealth…
LendingTree subsidiary QuoteWizard and automotive parts provider Advance Auto Parts have been revealed as victims of attackers who are trying…
Staying Sharp: Cybersecurity CPEs Explained Perhaps even more so than in other professional domains, cybersecurity professionals constantly face new threats….
Subpostmasters used pre-Horizon Capture software without any training from the Post Office, a failing that mirrors one of the causes…
The wait is finally over! The Cyber Express is thrilled to announce the much-anticipated return of World CyberCon, India Edition….
Christie’s data breach impacted 45,798 individuals Pierluigi Paganini June 10, 2024 Auction house Christie’s revealed that the data breach caused by…
A proof-of-concept (PoC) exploit has been released for a critical authentication bypass vulnerability in Veeam Backup Enterprise Manager. The vulnerability,…
Cryptocurrency users beware: a malicious ComfyUI node steals sensitive data like passwords, crypto wallet addresses, etc. Stay safe by using…
In today’s digital age, businesses and individuals rely on cloud services to store, manage, and access data more efficiently than…
The National Council of Statewide Interoperability Coordinators (NCSWIC) attempts to shed light on the significant duties and routine tasks performed…
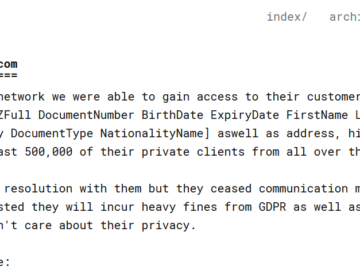
VIT Bhopal University, a leading academic institution in India, has allegedly been hit by a significant data breach, raising concerns…
RedSecLabs security researchers Rafay Baloch and Muhammad Samaak have uncovered address bar spoofing vulnerabilities in widely used mobile browsers such…