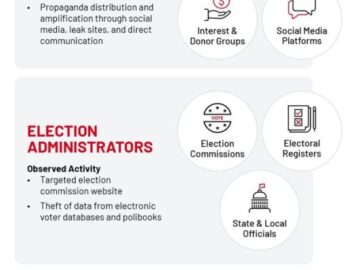
With more than 2 billion voters ready to cast a vote this year across 60 plus nations -including the U.S.,…
Recent years have witnessed a dramatic surge in cyberattacks, with both the frequency and sophistication of attacks reaching unprecedented levels….
By Alex Serdiuk, CEO, Respeecher Newer and more impactful technological advancements are making the quest for foolproof cybersecurity measures more…
APIContext has unveiled its 2024 Cloud Service Provider API Report, offering an in-depth examination of the performance of leading cloud…
Some router models have identified a security vulnerability that allows attackers to bypass authentication. To exploit this vulnerability, an attacker…
As the number of applications and systems used in businesses grows, so do the threats and vulnerabilities that can lead…
Microsoft announced revenue of $61.9bn for the quarter which ended 31st March 2024, representing an increase of 17% over the…
Cryptocurrencies and cybercrime: A critical intermingling Pierluigi Paganini April 26, 2024 As cryptocurrencies have grown in popularity, there has also…
Autodesk Drive is a data-sharing platform for organizations to share documents and files in the cloud. It also supports 2D…
DDoS attacks are a significant and growing risk that can overpower websites, crash servers, and block out authorized users with…
As we progress through 2024, home security is rapidly advancing, with a notable shift towards integrated residential security solutions. These…
Apr 26, 2024NewsroomNetwork Security / Zero Day Palo Alto Networks has shared remediation guidance for a recently disclosed critical security…