The European Parliament has overwhelming approved measures to ensure millions of people working for gig economy platforms have their employment…
Kaiser Permanente data breach may have impacted 13.4 million patients Pierluigi Paganini April 26, 2024 Healthcare service provider Kaiser Permanente…
The Cactus ransomware gang has been exploiting vulnerable Qlik sense servers ever since November 2023 using multiple vulnerabilities such as…
Hackers often target CrushFTP servers as they contain sensitive data and are used for file sharing and storage. This makes…
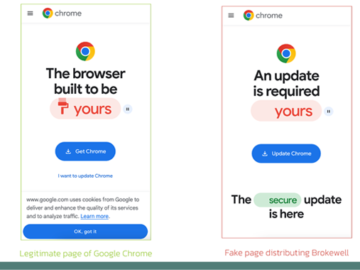
Apr 26, 2024NewsroomMobile Security / Cybercrime Fake browser updates are being used to push a previously undocumented Android malware called…
Cato Networks, the SASE leader, today announced that Cato CTRL, the SASE leader’s cyber threat intelligence (CTI) research team, will…
The telecom company AeroNet Wireless announced the launch of its new 10Gbps speed Internet plan, marking an important landmark for…
In today’s digital world, where connectivity is rules all, endpoints serve as the gateway to a business’s digital kingdom. And…
The Los Angeles County Department of Health Services disclosed a data breach after thousands of patients’ personal and health information…
A former subpostmaster forced senior Post Office executives to meet him to discuss his unexplained shortfall, but they then “lied”…
American private equity firm Thoma Bravo has inked an agreement to acquire British cybersecurity giant Darktrace for $4.6bn. This all-cash…
Healthcare service provider Kaiser Permanente disclosed a data security incident that may impact 13.4 million people in the United States….