In this Help Net Security interview, Assaf Mischari, Managing Partner, Team8 Health, discusses the risks associated with GenAI healthcare innovations…
In this article, you will find excerpts from reports we recently covered, which offer stats and insights into the challenges…
Did you always think you would work in the technology industry? After finishing my undergraduate degree at UC Berkeley, I…
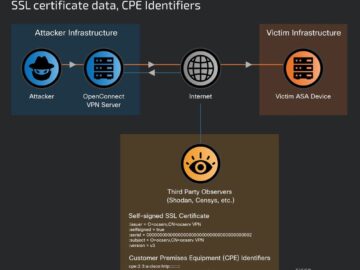
Nation-state actors exploited two zero-days in ASA and FTD firewalls to breach government networks Pierluigi Paganini April 24, 2024 Nation-state…
Keonne Rodriguez and William Lonergan Hill have been charged by the U.S. Department of Justice for laundering more than $100…
Did you know we’ve teamed up with our friends at PortSwigger to offer free 90-day licenses for Burp Suite Professional?…
Proof-of-concept exploit code has been released for a top-severity security vulnerability in Progress Flowmon, a tool for monitoring network performance…
Introducing a multifactor authentication (MFA) mandate for users of its platform has paid off for GitHub, which has reported a…
A state-sponsored threat actor has managed to compromise Cisco Adaptive Security Appliances (ASA) used on government networks across the globe…
SOC 2 compliance is based on evaluating a set of Trust Services Criteria (TSC). These criteria are grouped into five…
In an alarming revelation, officials from the Minnesota-based UnitedHealth Group disclosed on Monday that the health insurance and services giant…
Cisco warned today that a state-backed hacking group has been exploiting two zero-day vulnerabilities in Adaptive Security Appliance (ASA) and…