CrushFTP disclosed a zero-day vulnerability (CVE-2024-4040) affecting versions below 10.7.1 and 11.1.0. The vulnerability allows remote attackers with low privileges…
AI-powered generative tools have supercharged phishing threats, so even newbie attackers can effortlessly create refined, individualized campaigns. Protecting data and…
24 Apr An MSSP Shares the Latest in Ransomware: What’s Up, and What to Do About It What are the…
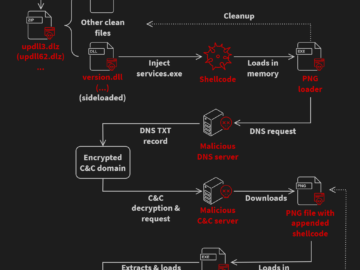
Apr 24, 2024NewsroomMalware / Endpoint Security Cybersecurity researchers have discovered an ongoing attack campaign that’s leveraging phishing emails to deliver…
A bill giving TikTok’s China-based owner ByteDance until January 2025 to sell up or get out of town has sailed…
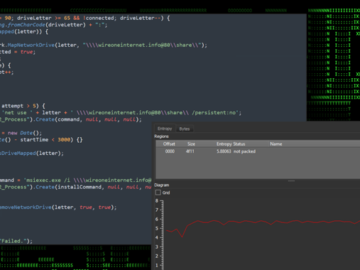
Hackers hijacked the eScan Antivirus update mechanism in malware campaign Pierluigi Paganini April 24, 2024 A malware campaign has been…
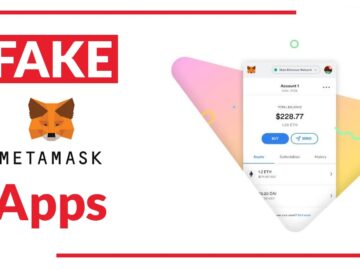
Threat actors exploit fake Android apps primarily for illicit reasons, such as stealing sensitive and personal information from unsuspecting users….
This campaign is observed to be targeting multiple countries, including the U.S., Nigeria, Germany, Egypt, the U.K., Poland, the Philippines,…
24 Apr The Rise In CISO Job Dissatisfaction – What’s Wrong And How Can It Be Fixed? Posted at 09:42h…
Apr 24, 2024NewsroomCyber Attack / Cyber Espionage The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) on Monday sanctioned…
Toronto-based artificial intelligence (AI) consultancy Crater has saved around CAN$1.5m (£885,000) in researcher time after it replaced difficult-to-configure direct-attached storage…
A significant vulnerability was detected in IBM QRadar Suite Software and Cloud Pak for Security, allowing attackers to execute arbitrary…