Hackers primarily use ransomware to gain financial gain from their victims by blackmailing them for payments to recover their encrypted…
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryptocurrency…
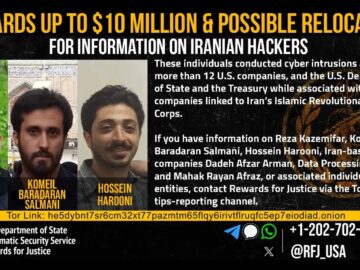
US offers a $10 million reward for information on four Iranian nationals Pierluigi Paganini April 24, 2024 The Treasury Department’s Office…
A new type of malware dubbed “Wavestealer” has been identified. This malicious software reportedly steals sensitive information such as login…
The United States Justice Department has announced big rewards for information leading to the capture of four Iranian nationals. These…
Alert fatigue represents more than a mere inconvenience for Security Operations Centre (SOC) teams; it poses a tangible threat to…
Change Healthcare, a subsidiary of UnitedHealth Group, has confirmed the transfer of 350 bitcoins, equivalent to $22 million USD, to…
The federal government has been asked to tweak the conditions for co-funding of telecommunications infrastructure in regional and remote Australia…
In today’s digital landscape, small and medium enterprises (SMEs) are increasingly turning to cloud computing to streamline operations, enhance scalability,…
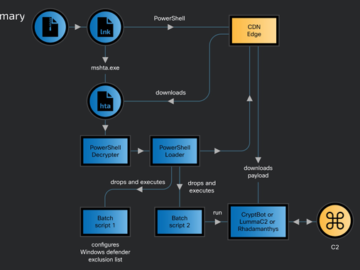
Apr 24, 2024NewsroomMalware / Data Security A new ongoing malware campaign has been observed distributing three different stealers, such as…
One of the biggest concerns over generative AI is its ability to manipulate us, which makes it ideal for orchestrating…
McLeod Cranes hires artificial intelligences to take heat out of safety incidents When things go pear-shaped with a 350-ton…