In the television show Arrow, billionaire playboy Oliver Queen returns to Star City after being trapped on an island only…
“Make tape easy.” That’s the rallying call from Fujifilm, which says this is key to getting more organisations to use…
The National Police Agency in South Korea issued an urgent warning today about North Korean hacking groups targeting defense industry…
0G Labs and One Piece Labs have announced the launch of the first incubator for startups working at the intersection…
A former consultant at Sellafield has claimed that metadata in letters used against her in a tribunal hearing by the…
Beware! Cybercriminals are exploiting an open redirect vulnerability for phishing attacks that impersonate Nespresso to steal Microsoft logins. Millions of…
Veeam, a leading provider of backup solutions, has announced its acquisition of Coveware, a cyber incident response firm, in a…
The Russia-backed advanced persistent threat (APT) operation tracked as Forest Blizzard by Microsoft – but more commonly known as Fancy…
The Department of State has started imposing visa restrictions on mercenary spyware makers and peddlers, prohibiting their entry into the…
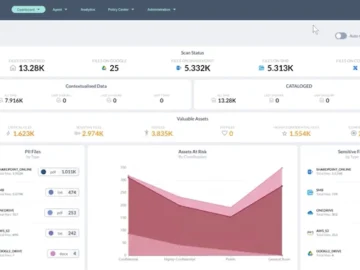
Forcepoint has launched Forcepoint Data Security Posture Management (DSPM), driven by AI to deliver real-time visibility, ease privacy compliance and…
Apr 23, 2024NewsroomSupply Chain Attack / Application Security Researchers have identified a dependency confusion vulnerability impacting an archived Apache project…
The latest data from analyst Gartner shows a 10% spike in the datacentre market, driven predominantly by hyperscalers deploying artificial…