North Korean hackers have been exploiting the updating mechanism of the eScan antivirus to plant backdoors on big corporate networks and…
Cybersecurity is ‘inclusive’ by nature: no one is exempt from the fallout of the expanding cyber threat landscape. The notion,…
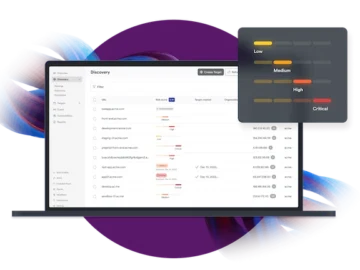
Invicti announced its new AI-enabled Predictive Risk Scoring capability. The feature assigns predicted risk to applications and helps organizations gain…
UnitedHealth Group has given an update on the February cyberattack on Change Healthcare, one of its subsidiaries. In the update,…
Austria’s success in artificial intelligence (AI) research and development largely stems from an academic realm of young thinkers, budding entrepreneurs…
The UnitedHealth Group has confirmed that it paid a ransom to cybercriminals to protect sensitive data stolen during the Optum…
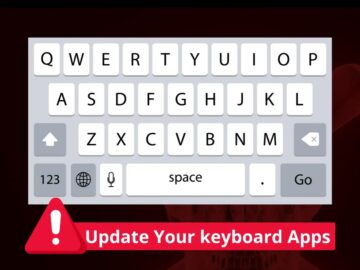
Researchers have uncovered critical security vulnerabilities in several widely used keyboard apps, including those from major tech giants Samsung, OPPO,…
Thanks to AI, phishing attacks are better than ever. So is our ability to stop them. By Antonio Sanchez, Principal…
Mandiant, part of Google Cloud, today released the findings of its M-Trends 2024 report. Now in its 15th year, this…
When cyber attacks strike, it’s rarely a single computer that suffers. Nowadays, cybercriminals set their sights on corporate networks, aiming…
23 Apr Unmasking The True Cost Of Cyberattacks: Beyond Ransom And Recovery Posted at 09:36h in Blogs by Di Freeze…
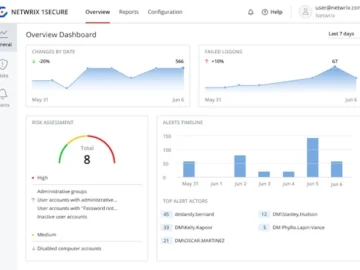
Netwrix released a new version of its IT auditing software-as-a-service (SaaS) solution, Netwrix 1Secure. It enables prompt detection of suspicious…