Former Post Office CEO Paula Vennells asked her husband for advice on how to refer to Horizon bugs in an…
Residents of Leicester have been facing an unusual urban phenomenon: street lights that stay lit day and night. This issue…
Oracle Virtualbox was identified and reported as having a critical vulnerability associated with Privilege Escalation and Arbitrary File Move/Delete. This…
McAfee cybersecurity researchers have discovered a malicious scheme exploiting GitHub’s comment section, where threat actors host malware and disguise download…
Edge computing is no longer a mere concept; it’s a reality that’s reshaping industries and transforming how we approach mobile…
Apr 23, 2024The Hacker NewsThreat Hunting / Software Security In the high-stakes world of cybersecurity, the battleground has shifted. Supply…
In January of this year I was prompted by Microsoft’s admission of a successful attack by Russia-backed hacking group Midnight…
A sophisticated malware campaign has been compromising the update mechanism of eScan antivirus software to distribute malicious backdoors and cryptocurrency…
To combat the misuse of commercial spyware, the United States Department of State has announced visa restrictions on 13 individuals…
Apr 23, 2024NewsroomCounterintelligence / National Security German authorities said they have issued arrest warrants against three citizens on suspicion of…
Thank you for joining! Access your Pro+ Content below. 23 April 2024 How data keeps Britain’s trains on track Share…
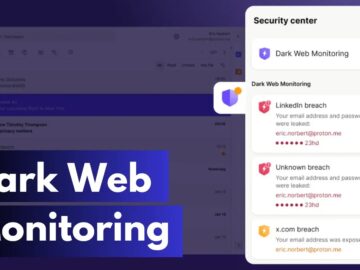
Proton Mail has introduced a new feature to enhance the safety of its users’ online identities. The new Dark Web…