Four billions public Discord messages are for sale on an internet scraping service called Spy.pet. At first sight there doesn’t…
The hacker group known as TransparentTribe, also referred to as APT-36, has intensified its cyber espionage activities. This group, originating…
A zero-day exploit targeting the popular messaging app WhatsApp has been advertised on underground hacker forums. The exploit has raised…
The depth of activities within software development ranges from ideation and design to coding, testing, and deployment. The cost of…
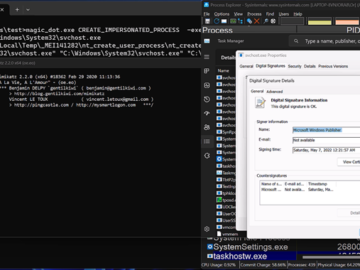
Windows DOS-to-NT flaws exploited to achieve unprivileged rootkit-like capabilities Pierluigi Paganini April 22, 2024 Researcher demonstrated how to exploit vulnerabilities…
Advanced Cyber Defence Systems (ACDS) has unveiled its groundbreaking Attack Surface Management (ASM) solution: OBSERVATORY. Engineered with a comprehensive three-pronged…
CrushFTP is a file transfer server that supports secure protocols, offers easier configuration, and offers powerful monitoring tools. It also…
Apr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by…
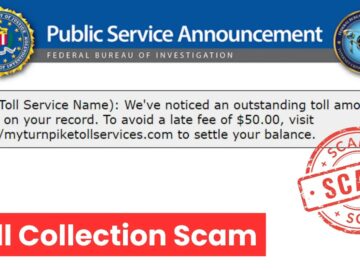
The FBI’s Internet Crime Complaint Center (IC3) has warned about a sophisticated smishing scam targeting drivers across multiple states. Since…
Cybersecurity experts from SafeBreach have revealed a series of vulnerabilities that could allow attackers to remotely delete files on a…
April 18, 2024 – A major international law enforcement effort has disrupted the notorious LabHost phishing-as-a-service platform. April 18, 2024…
Hackers are now offering administrative access to over 3000 Fortinet SSL-VPN devices. This breach poses a significant threat to the…