With the tightening grip of Chinese regulatory measures on foreign digital services, Apple Inc. has removed several major messaging apps,…
Citrix’s uberAgent, a sophisticated monitoring tool used to enhance performance and security across Citrix platforms, has been identified as having…
European Union Aviation Safety Agency (EASA) has issued a cautionary alert following reports of cyber-attacks targeting flights bound for the…
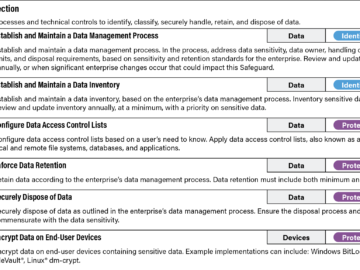
In this article, we’ll identify some first steps you can take to establish your cloud security strategy. We’ll do so…
Apr 22, 2024NewsroomCryptocurrency / Artificial Intelligence Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial…
A flaw in the Forminator plugin impacts hundreds of thousands of WordPress sites Pierluigi Paganini April 22, 2024 Japan’s CERT…
We’re pleased to share that our External Attack Surface Management (EASM) solution is now available on AWS Marketplace through private…
Some file names gave away clues about the series and episode numbers. There were also files and projects the researchers…
In today’s digital age, email has become an indispensable tool for communication, both personal and professional. Among the most widely…
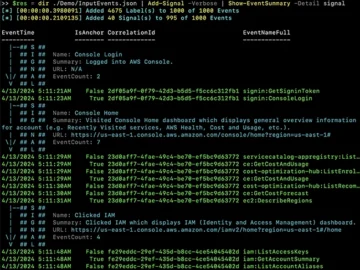
Cloud Console Cartographer is an open-source tool that maps noisy log activity into highly consolidated, succinct events to help security…
In this Help Net Security interview, Roy Davis, Manager – Vulnerability Management & Bug Bounty at Zoom, discusses the role…
Most compliance leaders tend to focus on building an ethical culture in their organizations to improve employee behavior, but it…