Apr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to…
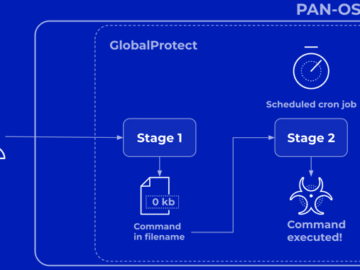
Apr 20, 2024NewsroomVulnerability / Network Security Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS…
While ransomware attacks decreased after the LockBit and BlackCat disruptions, they have once again started to ramp up with other…
MITRE revealed that nation-state actors breached its systems via Ivanti zero-days Pierluigi Paganini April 19, 2024 The MITRE Corporation revealed…
CrushFTP warned customers today in a private memo of an actively exploited zero-day vulnerability fixed in new versions released today,…
The United Nations Development Programme (UNDP) is investigating a cyberattack after threat actors breached its IT systems to steal human…
The Safous Zero Trust Access (ZTA) solution emerges as a comprehensive cybersecurity platform, designed to tackle the growing challenges enterprises…
An operator of the HelloKitty ransomware operation announced they changed the name to ‘HelloGookie,’ releasing passwords for previously leaked CD…
The MITRE Corporation says that a state-backed hacking group breached its systems in January 2024 by chaining two Ivanti VPN…
Two of the biggest deepfake pornography websites have now started blocking people trying to access them from the United Kingdom….
The FBI, in collaboration with CISA, Europol European Cybercrime Centre, and the Netherlands NCSC, has issued a stark warning regarding…
Approximately 22,500 exposed Palo Alto GlobalProtect firewall devices are likely vulnerable to the CVE-2024-3400 flaw, a critical command injection vulnerability…