Bots compose 42% of overall web traffic, and 65% of these bots are malicious, according to Akamai. Negative effects of…
Here’s a look at the most interesting products from the past week, featuring releases from ARMO, Cofense, Datadog, and eSentire….
On Wednesday, June 26, 2024, TeamViewer, a leading provider of remote access software, announced that attackers had compromised its internal…
A data security officer from the Manila Bulletin has admitted to hacking 93 websites, including government and private company sites,…
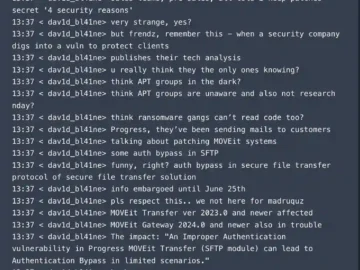
A newly disclosed vulnerability in Progress MOVEit Transfer has sparked concern among cybersecurity experts due to the lingering memory of…
A threat actor tracked as Unfurling Hemlock has been infecting target systems with up to ten pieces of malware at the…
Image: Midjourney The BlackSuit ransomware gang claimed a recent cyberattack on KADOKAWA corporation and is now threatening to publish stolen…
We believe in fostering an environment where everyone feels valued and empowered to be their authentic selves, both in and…
The Black Suit ransomware gang claimed a recent cyberattack on KADOKAWA corporation and is now threatening to publish stolen data…
Amazon’s cloud division has launched an investigation into Perplexity AI. At issue is whether the AI search startup is violating…
Queensland Rail has recruited Darren Cavanagh from Transport for NSW as its group executive of digital and information. Queensland Rail…
Crypto scammers hijacked Channel 7 News Australia’s YouTube account to run a live stream of an Elon Musk deepfake on…