The Halo Trust is tapping into Amazon Web Services’ (AWS’s) portfolio of artificial intelligence (AI) tools for a pilot project…
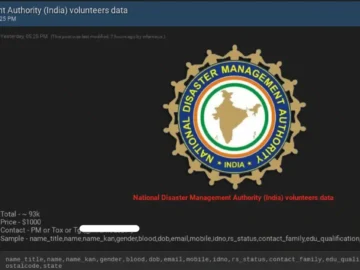
A threat actor claims to have carried out a cyberattack on India’s National Disaster Management Authority (NDMA). The NDMA is…
Infinidat, a leading provider of enterprise storage solutions, has introduced a new automated cyber resiliency and recovery solution that will…
Infinidat, a leading provider of enterprise storage solutions, has introduced a new automated cyber resiliency and recovery solution that will…
On June 24, we observed a new campaign distributing a stealer targeting Mac users via malicious Google ads for the…
Infinidat, a leading provider of enterprise storage solutions, has introduced a new automated cyber resiliency and recovery solution that will…
A new variant of the Medusa malware family was discovered disguised as a “4K Sports” app, which exhibits changes in…
We live in an era where social media is being ruled by Facebook, Instagram, TikTok and Twitter (X), but a…
27 Jun July Is Ransomware Awareness Month Posted at 08:58h in Blogs by Di Freeze This week in cybersecurity from…
Apple has taken steps to enhance the security of its popular AirPods lineup by addressing a critical Bluetooth vulnerability through…
A Proof-of-Concept (PoC) exploit has been released for a critical SQL Injection vulnerability in Fortra FileCatalyst Workflow. This vulnerability could…
Waltham, Massachusetts, June 27th, 2024, CyberNewsWire Infinidat, a leading provider of enterprise storage solutions, has introduced a new automated cyber…