A former Fujitsu engineer who gave evidence for the Post Office during trials of subpostmasters has made an “extraordinary” claim…
Cybersecurity researchers at K7 Labs have uncovered a new threat targeting Telegram users. The malicious software, SpyMax, is a Remote…
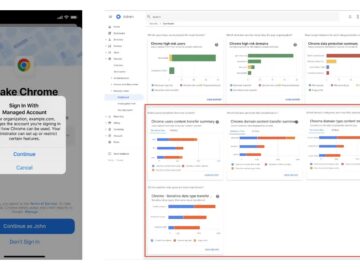
Google has unveiled new features for Chrome Enterprise Core, formerly known as Chrome Browser Cloud Management. As organizations increasingly rely…
Apple has recently released critical firmware updates for its AirPods and Beats headphones to address a significant Bluetooth vulnerability. The…
Multiple vulnerabilities have been identified in the TP-Link Omada system, a software-defined networking solution widely used by small to medium-sized…
A federal grand jury in Maryland returned an indictment charging a Russian citizen with conspiracy to hack into and destroy…
Jun 27, 2024NewsroomVulnerability / Enterprise Security A critical security flaw has been disclosed in Fortra FileCatalyst Workflow that, if left…
The 2024 Paris Olympics is set to begin on July 26, global adversaries are paying close attention and such a…
In collaboration with the Federal Bureau of Investigation (FBI), Australian Signals Directorate’s Australian Cyber Security Centre (ACSC), and Canadian Cyber…
Evolve Bank & Trust disclosed that it has been the target of a cybersecurity incident. In a statement, the bank…
New P2Pinfect version delivers miners and ransomware on Redis servers Pierluigi Paganini June 27, 2024 Researchers warn that the P2Pinfect…
According to a joint investigation by security analysts from SentinelOne and Recorded Future, a significant ransomware campaign targeted government and…