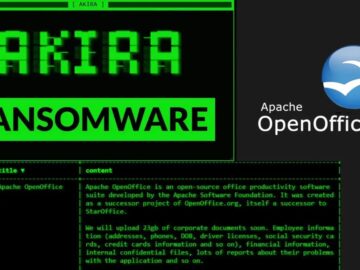
The notorious Akira ransomware gang announced on October 29, 2025, that it successfully penetrated the systems of Apache OpenOffice, claiming…
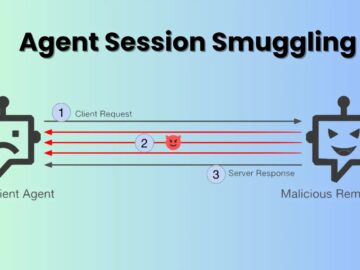
Security researchers have uncovered a sophisticated attack technique that exploits the trust relationships built into AI agent communication systems. The…
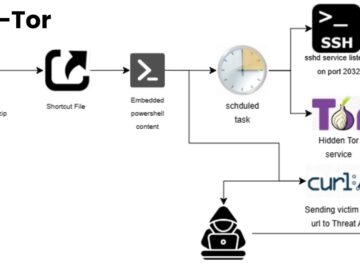
In October 2025, cybersecurity researchers at Cyble Research and Intelligence Labs (CRIL) uncovered a sophisticated malware campaign distributing weaponized ZIP…
The U.S. Cybersecurity and Infrastructure Security Agency has added a critical Linux kernel vulnerability to its Known Exploited Vulnerabilities catalog,…
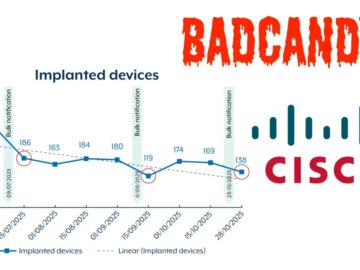
Cybersecurity authorities are raising urgent alarms as threat actors continue to exploit a critical vulnerability in Cisco IOS XE devices,…
Cybercriminals and state-sponsored actors are ramping up attacks on unpatched Cisco IOS XE devices across Australia, deploying a persistent Lua-based…
The notorious Akira ransomware group announced on October 29, 2025, that it successfully breached the systems of Apache OpenOffice, exfiltrating…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert about a critical use-after-free vulnerability in the…
Windows Server Update Services (WSUS) vulnerability is actively exploited in the wild. Criminals are using this vulnerability to steal sensitive…
In a surprise raid on Thursday, October 30, 2025, Russian law enforcement detained three individuals suspected of creating and selling…
Federal law enforcement said a leader of 764, a violent extremist group, has been in federal custody since he was…
If you have two headphones, speakers, or any other Bluetooth hardware, you can now share audio between the two devices…