A threat actor known as “phant0m” is promoting a new Ransomware-as-a-Service (RaaS) on OnniForums, a notorious dark web forum. The…
Okta warns of credential stuffing attacks targeting its Cross-Origin Authentication feature Pierluigi Paganini May 30, 2024 Identity and access management…
Cybersecurity researchers have released a Proof-of-Concept (PoC) exploit for a recently disclosed information disclosure vulnerability in Microsoft Edge, the Chromium-based…
In a shocking revelation, a threat actor has allegedly leaked sensitive data belonging to Shell, one of the world’s leading…
BBC Data Breach Exposes Personal Information of 25,000 Staff Members In a recent development, a spokesperson from BBC Pension issued…
An 18-year-old high school student from Texas has found himself at the center of a significant cybercrime investigation. Keontra Kenemore…
Engaging Work Perfect to deliver a solution that leverages monday.com and Jira has paid dividends for leading banking and payments…
The National Institute of Standards and Technology (NIST) is launching a new testing, evaluation, validation and verification (TEVV) program intended…
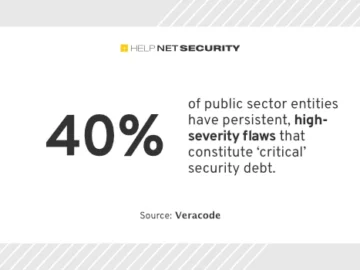
Applications developed by public sector organizations have more security debt than those created by the private sector, according to Veracode….
Check Point, a leading cybersecurity vendor, has released emergency patches to address a critical zero-day vulnerability in its VPN products…
With the rise of identity sprawl and system complexity, more businesses are suffering identity-related incidents than ever before, according to…
Uncover IT security weaknesses and ensure compliance with infosec audits. Regular audits protect your data from breaches & meet regulations….